Fabian has just completed his PhD at New York University with focus on programmable networks. He is now joining Xsight Labs where he will be working on the SDK for the X2 programmable networking chip. The following text is a blog post based on his dissertation, which is available here: https://cs.nyu.edu/media/publications/ruffy_fabian_dissertation.pdf
Using P4 for Static Analysis of Network Device Stacks
Programmability in computer networks is evolving. Merchant silicon and network programming languages like P4 give us remarkable flexibility, but this flexibility comes at a cost: the software stack running on network devices—responsible for packet forwarding and interpreting control plane instructions—has grown substantially more complex. This complexity can introduce faults, which can take down entire networks. Traditional network verification techniques can check network-wide properties like reachability or loop-freedom, but these tools often assume that individual devices execute forwarding entries correctly. This assumption is less tenable as device stacks become deeper and more intricate. There’s a clear need for network-device verification, focusing on the functional correctness of the software stack within a single device. Figure 1 illustrates this distinction.
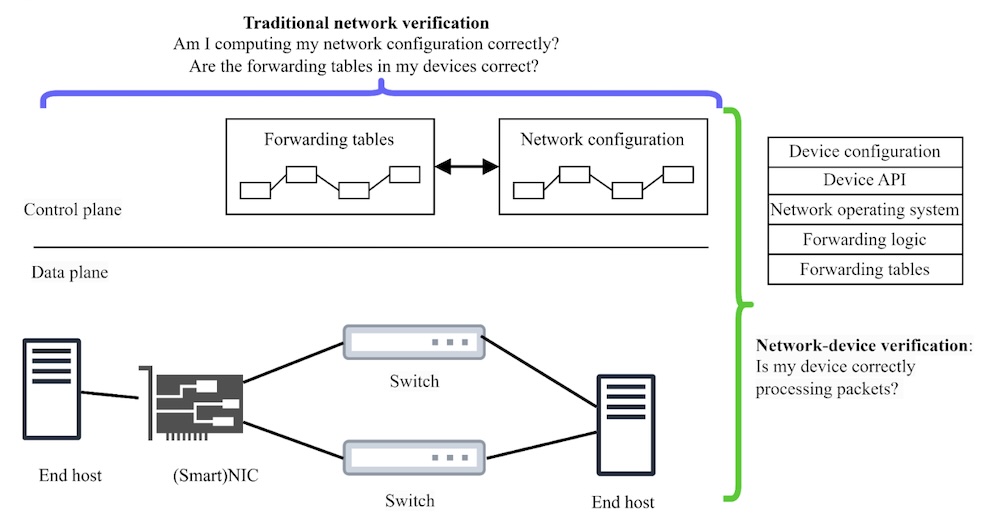
Figure 1: Traditional horizontal network verification vs vertical network-device verification.
General-purpose static analysis tools to check networking stacks exist, but they often struggle. Languages like C++ or Python, common in device stacks, make precise analysis difficult or computationally expensive because of the presence of pointers, aliasing, and complex control flow. General tools also lack awareness of the specific constraints and execution models inherent in packet processing hardware. Attempting to verify device stacks requires a different approach—one that captures the nuances of packet processing from the hardware pipeline up to the software abstract layers.
The P4 Advantage: A Foundation for Static Analysis
Our work explores using P4 itself as a foundation for building effective static analysis tools. P4 is not just a language for programming data planes; its design implicitly encodes a model of packet processing suitable for formal analysis. Several properties make P4 amenable to this approach:
- Restricted Semantics: P4 deliberately omits features common in general-purpose languages, such as general loops, aliasing, dynamic memory allocation, and complex pointer arithmetic. This restriction simplifies the development of precise semantic models.
- Explicit Execution Model: P4 programs typically target hardware pipelines with specific constraints (e.g., run-to-completion, fixed time budgets). The language structure reflects these constraints, providing a clearer model for analysis.
- Decidability: The finite-state nature of many P4 constructs can make challenging problems like program equivalence decidable, which in turn can enable better automated verification techniques compared to general-purpose languages.
Our Approach: An SMT-Based Execution Model
We use P4’s properties to develop an execution model for P4 based on Satisfiability Modulo Theories (SMT). We translate P4 language constructs and architecture behaviors into SMT formulas. This model is designed to be:
- Protocol-Independent: Like P4, we represent packet processing using primitives like arithmetic, table lookups, and state manipulation via registers, rather than being tied to specific network protocols.
- Device-Agnostic: We capture P4 semantics as defined in the official specification and include extension mechanisms to model specific device behaviors accurately.
- Precise: Our approach produces a test oracle. We do not require a second compiler or device model to perform our testing. We also do not require developer-written assertions to generate tests. Since the model is bit-level accurate we can also detect subtle bugs.
Applying the Model: Three Tools
We developed and applied this SMT-based model across three distinct projects, each addressing a different aspect of network device stack analysis:
- Gauntlet: Focuses on testing P4 compilers. It uses translation validation (comparing SMT models of code before and after compiler passes) and random P4 program generation to find compiler crashes and miscompilations. The paper is available here.
- P4Testgen: Acts as an extensible test oracle. It generates high-fidelity input packets, control-plane configurations, and expected output packets to test the entire device stack’s implementation of a P4 program by modeling detailed target-specific semantics. The paper is available here.
- Flay: Optimizes P4 programs using incremental specialization. It uses our SMT model, extended with control-plane semantics (based on P4Runtime), to simplify data-plane forwarding logic based on the current control-plane configuration, This tool recompiles only when necessary. The paper is available here.
Each tool builds on the previous one, progressively developing a more comprehensive execution model. Gauntlet models the P4 language core. P4Testgen adds device behavior and whole-program semantics. Flay incorporates the influence of the control plane. Figure 2 shows the expanding scope of the execution model across these tools.
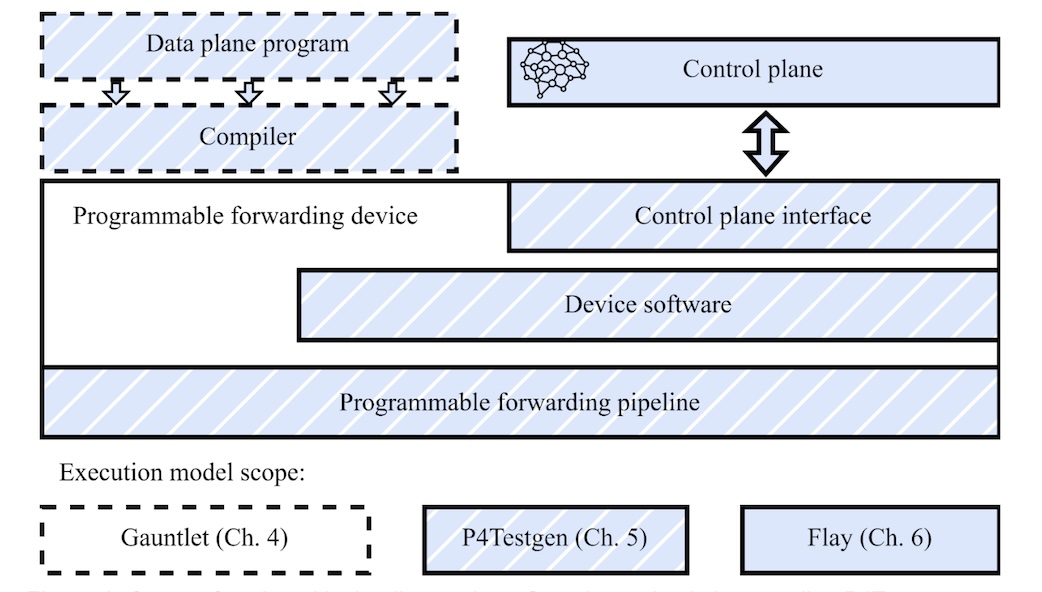
Figure 2: Scope of each tool in the dissertation – Gauntlet to check the compiler; P4Testgen to generate tests; Flay to optimize network programs.
Impact and Open Contributions
We used our P4-based static analysis approach with Gauntlet to identify approximately 100 unique, confirmed P4 compiler bugs (crashes and miscompilations). P4Testgen and Flay, using the extended model, uncovered around 30 additional confirmed bugs related to incorrect packet processing within device stacks (including compilers, control plane interactions, and target models). Flay also demonstrated significant resource savings (e.g., 20% stage reduction in a Tofino 2 program) through control-plane-aware specialization.
All tools developed from this research (Gauntlet’s components, P4Testgen, Flay’s prototype, and supporting tools like the control-plane fuzzer RTSmith) have been contributed back to the P4 community as open-source projects, primarily integrated within the P4C repository and related projects. This work heavily benefited from the openness of the P4 language, its specifications (like P4Runtime), and the surrounding tooling (P4C, BMv2). For us, the ecosystem was essential for developing, validating, and sharing these analysis techniques.
We believe this approach demonstrates the value of using domain-specific languages like P4 not just for programming, but also as a basis for rigorous analysis of the increasingly complex systems they run on.
If you are interested in learning more about these techniques and tools, the full dissertation is available here: https://cs.nyu.edu/media/publications/ruffy_fabian_dissertation.pdf If you have questions, reach out to Fabian at contact@ruffy.eu.
P.S.:
A German doctoral tradition is for the newly minted doctor to receive a PhD hat themed based on their focus area and hobbies after a successful defense. Here is Dr. Ruffy with his Doktorhut, appropriately themed around computer networking.

